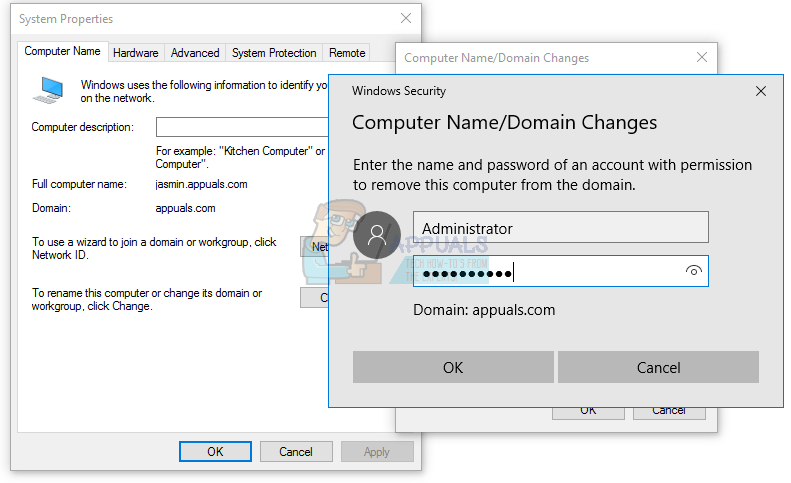
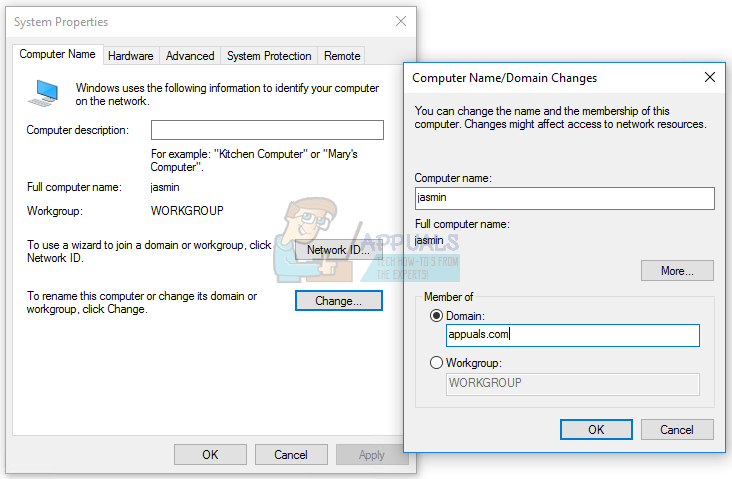
Security and network administrators are increasingly wary of internal security threats, in addition to threats from the outside, due to the introduction of uncertified hardware and software on the network, such as personal portable computers and mobile devices that can be potentially compromised and not compliant to the security practices of the organization. Link layer-based filtering for Dynamic Host Configuration Protocol (DHCP) introduced in Windows Server 2008 R2 enables administrators to control network access based on media access control (MAC) address, providing a low-level security method. The link layer filtering controls allow the administrator to specify which MAC addresses are allowed on the network and which are denied access. You can use wild cards to allow or deny network access based on vendor MAC prefixes.
DHCP PowerShell introduced in Windows Server 2012 makes it very easy and seamless for admins to manage Link Layer filtering for IPv4 clients.
Following cmdlets are provided to manage Link Layer Filtering in DHCP Server:
Get-DhcpServerv4FilterList: Gets the enabled/disabled state of allow and deny filter list set.
Set-DhcpServerv4FilterList: Enables/Disables the allow and the deny MAC address filter lists.
Get-DhcpServerv4Filter: Gets the list of all MAC addresses from the allow and/or the deny list.
Add-DhcpServerv4Filter: Adds one or more MAC address filters to the allow or deny list.
Remove-DhcpServerv4Filter: Removes the specified MAC address or MAC address pattern from the allow list or the deny list of the DHCP server.
If you wan to add a large list of MAC addresses to the allow or deny filter list, an input text file in CSV format can be used to provide the MAC address filter list to be configured on the DHCP server. This data can be easily pipelined to Add-DhcpServerv4Filter cmdlet to add the complete list to the DHCP Server. The input text file (filter.csv in the example used later) containing the MAC address filters should be of the following format -
List,MacAddress,Description
Allow,1a-1b-1c-1d-1e-1f,Filter for Computer1
Allow,2a-2b-2c-2d-2e-2f, Filter for Computer2
Deny,3a-3b-3c-3d-3e-3f, Filter for Computer3
Allow,4a-4b-4c-4d-4e-4f, Filter for Computer4
The following command adds all these filters to the local DHCP Server.
Import-Csv Filter.csv | Add-DhcpServerv4Filter -Force
The Import-Csv cmdlet converts each data record in filter.csv to an object containing List, MacAddress and Description as members of the object. Each object created by Import-Csv is sent through the pipeline to Add-DhcpServerv4Filter which adds the MAC address records to the filter list on the DHCP server.
‘-Force’ parameter ensures that if a filter by same MAC address already exists, it is over-ridden. If ‘-Force’ parameter is not given and MAC address being added to the list already exists in the list on the DHCP server, the cmdlet will return an error.
In case, filters need to be added to DHCP Server running on remote machine, ‘-ComputerName’ parameter can be used to specify remote DHCP Server. Without the ComputerName parameter, as in the example above, the filters will be added to the DHCP server running on the local computer.
Oneway sync DHCP filter
list It looks like you can do a Get-DhcpServerv4FilterList and a Set-Dhcpv4FilterList. Schedule this in a Powershell script and you have a one-way sync.